From A To Z Projective Coordinates Leakage In The Wild
Publications The Cancer Imaging Archive Tcia

Online Template Attacks Springerprofessional De
Ecdsa Side Channel Attack Projective Signatures Ledger Donjon Ctf Writeup Cryptohack Blog
Alejandro Cabrera Acaldaya Twitter

Cesar Pereida Garcia S Research Works Tampere University Tampere Uta And Other Places
Manuscriptlink Society File S3 Ap Northeast 1 Amazonaws Com Kiisc Wisa Ec 98 A8 Eb 9d Ec 9d B8 Ed 94 84 Eb A1 9c Ec 8b 9c Eb 94 Pdf
Tum cohomology of the projective space (Iritani also showed that this can be extended to the quantum cohomology of Fano toric varieties or orbifolds) This is strongly related to the notion of TERP structure of Hertling 1 Tame versus wild in complex analytic geometry dimension one • ∆ disc, coord z • ∆ =e S1 ×0,1) real blowup.
From a to z projective coordinates leakage in the wild. Three‐dimensional visualization of the Earth's magnetic field topology in GSM coordinates computed using T96 model (Tsyganenko, 1996) at 924 UT in the x‐z plane (a) and in the y‐z plane (b), respectively The MMS orbit between 8 and 1100 and location between 0924 are shown in red line and by a (magnified) black circle, respectively. 813 Likes, 2 Comments UWMilwaukee (@uwmilwaukee) on Instagram “Happy #PantherPrideFriday 🐾💛 us in your photos to be featured on our page or in our Photos of”. Amplified when multiplied by the LWE secret s, it is essential to assume that s has small coordinates A major part of our reduction (Section 4) is therefore dedicated to showing a reduction from LWE (in dimension n) with arbitrary secret in Zn q to LWE (in dimension nlog 2 q) with a secret chosen uniformly over f0;1g This.
The damping of propagating waves and loop oscillations is currently a very hot topic, because we are just at the brink of learning which the underlying physical mechanisms are wave leakage (Cally 03;. Aschwanden et al 03;. Díaz et al 04), resonant absorption (VanDoorsselaere et al 04a;.
To prevent information leakage, zscore transformation was carried out independently for each sample and within each data set We trained 500 kNN models from zscored microarray training data using the approach depicted in Figure 1 c and directly applied the models to predict both microarray and RNASeq validation samples. 1 Introduction 11 History and background The subject of control is concerned with methods to manipulate the evolution of dynamical systems As such it is relevant to many fields both inside , , , , , and outside , physics Control has a long history, but it emerged as a modern scientific discipline only after the pioneering work of Norbert Wiener in the 1940s. Abstract Synchronous bursting (SB) is ubiquitous in neuronal networks and independent of network structure Although it is known to be driven by glutamatergic.
MethodOur model for pulse propagation in a hollow waveguide is based on paraxial approximation of the NLSE in the following form (see eg, Refs 7 and 8)∇ 2 ⊥ E(r, z, t) − 2 c ∂ 2 ∂z∂t E(r, z, t) = 1 0c 2 ∂ 2 ∂t 2 PNL(r, z, t),(1)where the first and second terms on the lefthand side stand for diffraction and space time. 2(α) in Z/2 to be the pushforwards of αvia the two projections to CH n(X)/2 ∼= Z/2 Here is our extension of Karpenko’s theorem 12, Theorem 64 to any characteristic The proof follows the original one but is modified in order to avoid the restriction to smooth quadrics For quasilinear quadrics, the original proof does. Page 1 advanced quadrature sets, acceleration and preconditioning techniques for the discrete ordinates method in parallel computi ng environments by gianluca longoni a dissertation presented to the graduate school of the university of flor ida in partial fulfillment of the requirements for the degree of doctor of philosophy university of florida 04.
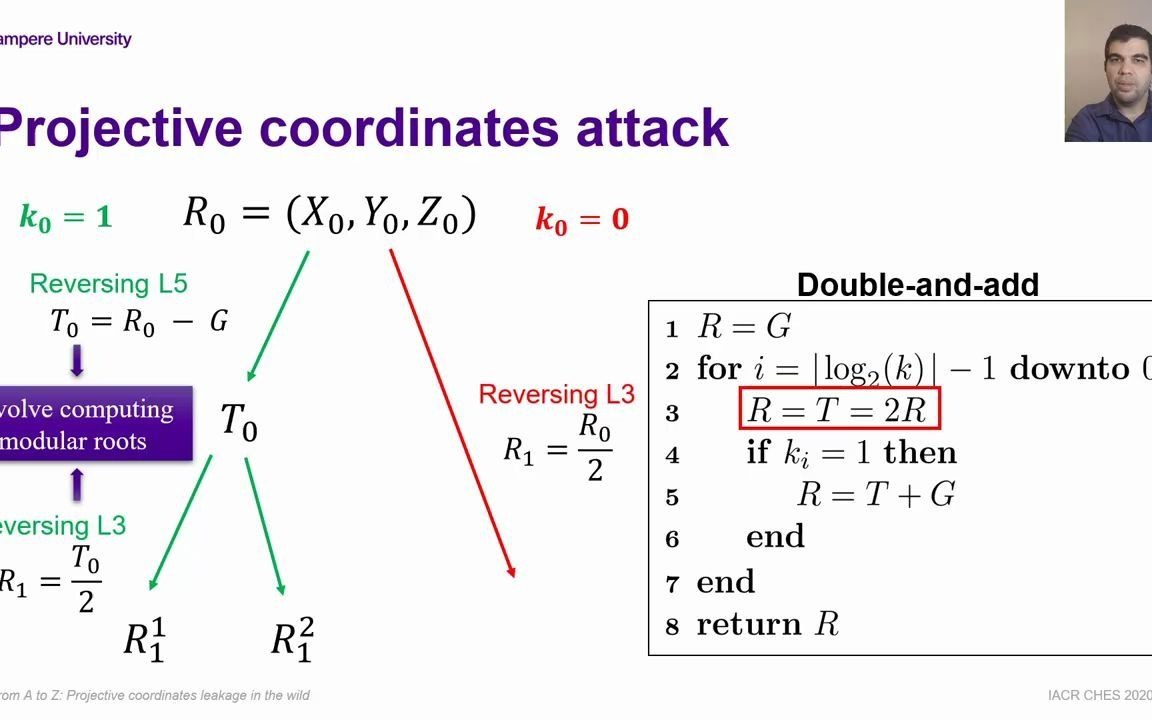
Such access might be granted to an adversary by a poor software implementation that does not erase the Z coordinate of P from the computer’s memory or. From A to Z Projective coordinates leakage in the wild Alejandro Cabrera Aldaya;. Less, LyC escape of galaxies at z ∼ 3 was reported by Iwata et al (09), Nestor et al (11), Mostardi et al (15) and Micheva, Iwata & Inoue (15), but could be suffering from foreground contamination(Sianaetal07;Vanzellaetal10)Sofar,themost convincing cases of LyC leakage in individual galaxies at high red.
Leakage in very faint galaxies at z ˘2 4 In this paper we present the detection of LyC photons in the afterglow spectrum of GRBB at z = We further investigate LyC emission in LGRB afterglow spectra, also adding to this case GRBs and A (z = and z = , respectively), the only two previously known GRBs. This dipole is meant to model leakage through a coaxial cable The halfwave dipole antenna was simulated using HFSS at a frequency of 1 GHz The length of a halfwave dipole antenna should be equal to λ/2, where λ is the operating wavelength Therefore, to Cartesian coordinates (x,y,z) Eq 1 was used for this purpose. We developed a threedimensional numerical model of LargeModeArea chirped pulse fiber amplifiers which includes nonlinear beam propagation in nonuniform multimode waveguides as well as gain spectrum dynamics in quasithreelevel active ions We used our model in tapered Ybdoped fiber amplifiers and showed that singlemode propagation is maintained along the taper even in the presence of.
In this case the exact WKB analysis leads to consideration of a new sort of Darboux coordinate system on a moduli space of flat \({\mathrm {SL}}(3)\)connections We give the simplest example of such a coordinate system, and verify numerically that in these coordinates the monodromy of the \(T_3\) equation has the expected asymptotic properties. Izi 2Z pz can be computed with O(nlogn) operations by FFT interpolation We will use the following Lemma while proving correctness of coefficients of a polynomial Lemma 2 (Schwartz–Zippel) Let pz;qz be two ddegree polynomials from Z pz Then for w $ Z p, the probability that p(w)=z(w) is at most d=p, and the equality can be tested. Paper From A to Z Projective coordinates leakage in the wild Authors Alejandro Cabrera Aldaya, Tampere University, Tampere, Finland Naccache et al showed that the projective coordinates representation of the resulting point of an elliptic curve scalar multiplication potentially allows to recover some bits of the scalar However, this.
Anthrax is rare in the United States, but outbreaks do occur in wild and domestic animals Yearly vaccination of animals is recommended in areas that have had anthrax in the past The disease is most common in parts of Central and South America, subSaharan Africa, central and southwestern Asia, southern and Eastern Europe, and the Caribbean. In , a Z / p Zcovering of an affine variety Spec A is investigated, and it is shown that if A is a noetherian factorial domain satisfying the condition that every projective Amodule of rank p, p − 1, p − 2 is free then every Z / p Zcovering of Spec A is given as Spec B, where B = A z / (z p − z − a) with a ∈ A. Ghost in the Shell Stand Alone Complex A variant appears in the episode "POKER FACE", where a flashback has the Major fire a shot down Saitou's.
Also we deduce that a mapping f ∈ H(B) has parametric representation if and only if there exists a Loewner chain f(z,t) such that the family {et f(z, t)} t ≥ 0 is a normal family on B and f(z) = f(z,0) for z ∈ B Finally we conclude that the set S 0 (B) of mappings which have parametric representation on B is compact. In an episode of Trigun Vash does one better and countersnipes a sniper down the barrel of his own gun — thus destroying the weapon without hurting the sniper Too bad the sniper is a fanatic who promptly pulls out a sidearm and shoots himself;. 1 Introduction 11 History and background The subject of control is concerned with methods to manipulate the evolution of dynamical systems As such it is relevant to many fields both inside , , , , , and outside , physics Control has a long history, but it emerged as a modern scientific discipline only after the pioneering work of Norbert Wiener in the 1940s.
In appropriate projective coordinates the Hesse pencil is given by the equation (1) λ (x 3 y 3 z 3) μxyz = 0 The pencil was classically known as the syzygetic pencil 2 of cubic curves (see 9, p 230 or 16, p 274), the name attributed to L Cremona. To remove DC leakage using preprocessing 2400, in certain embodiments the encoder side DC leakage is estimated 2410, and then, during the forward POT (eg, 800 at FIG 8), compensation is made for the leakage 23 (before the quantization process) at the encoder The same methods can be used that have already described herein for determining. The construction of Z is slightly involved, but on a high level, Z internally simulates the actions of Z~ including all ITIs activated by Z~ (other than those for G and the lth instance of ˇ), but forwards all communications sent to the lth instance of ˇto its own external interaction.
So leakage of coordinates of the NTT transform is a natural model for key exposure attacks NewHope key exchange protocol Some of our results focus on analysis of the NewHope key exchange protocol of 4 in the presence of partial key exposure Brie. Also we deduce that a mapping f ∈ H(B) has parametric representation if and only if there exists a Loewner chain f(z,t) such that the family {et f(z, t)} t ≥ 0 is a normal family on B and f(z) = f(z,0) for z ∈ B Finally we conclude that the set S 0 (B) of mappings which have parametric representation on B is compact. Amplified when multiplied by the LWE secret s, it is essential to assume that s has small coordinates A major part of our reduction (Section 4) is therefore dedicated to showing a reduction from LWE (in dimension n) with arbitrary secret in Zn q to LWE (in dimension nlog 2 q) with a secret chosen uniformly over f0;1g This.
Significance Mitochondria are the energetic, metabolic, redox, and information signaling centers of the cell Substrate pressure, mitochondrial network dynamics, and cristae morphology state are integrated by the protonmotive force Δp or its potential component, ΔΨ, which are attenuated by proton backflux into the matrix, termed uncouplingThe mitochondrial uncoupling proteins (UCP1–5. R/pokemon r/pokemon is an unofficial Pokémon fan community This is the place for most things Pokémon on Reddit—TV shows, video games, toys. The set of public keys in CSIDH is a subset of all supersingular elliptic curves defined over F p, in Montgomery form y 2 = x 3 A x 2 x, where A ∈ F p is called the Acoefficient of the curve 1 1 1 Following , we represent A = A ′ / C ′ as a projective point (A ′ C ′);.
Emergency evacuations are more common than many people realize, including evacuations in the workplace According to the US Department of Homeland Security (DHS) Federal Emergency Management Agency (FEMA), the most frequent causes of evacuations in the US each year are fires and floods In. The vulnerability is in particular present in several recent versions of OpenSSL However, it leaks less than 1 bit of information about the nonce, in the sense that it reveals the most significant bit of the nonce, but with probability. Significance Mitochondria are the energetic, metabolic, redox, and information signaling centers of the cell Substrate pressure, mitochondrial network dynamics, and cristae morphology state are integrated by the protonmotive force Δp or its potential component, ΔΨ, which are attenuated by proton backflux into the matrix, termed uncouplingThe mitochondrial uncoupling proteins (UCP1–5.
The OceanParcels project develops Parcels (Probably A Really Computationally Efficient Lagrangian Simulator), a set of Python classes and methods to create customisable particle tracking simulations using output from Ocean Circulation modelsParcels can be used to track passive and active particulates such as water, plankton, plastic and fish The code from the OceanParcels project is licensed. WT, wild type Cell death was quantified by a leaf disk ion leakage (conductivity) assay at 3 days after agroinfiltration (dai) Data are normalized to the mean value for samples with RPP1_WsB and WT ATR1_Emoy2 in each experiment. For example, from the model data in Figure 15a, for Z = 01 and N D = 4, a % decrease in path length can lead to a 5‰ decrease in vein δ 18 O However, above the isotopic front, for example at Z = 06, a % decrease in reactive path length decreases vein δ 18 O by less than 1‰.
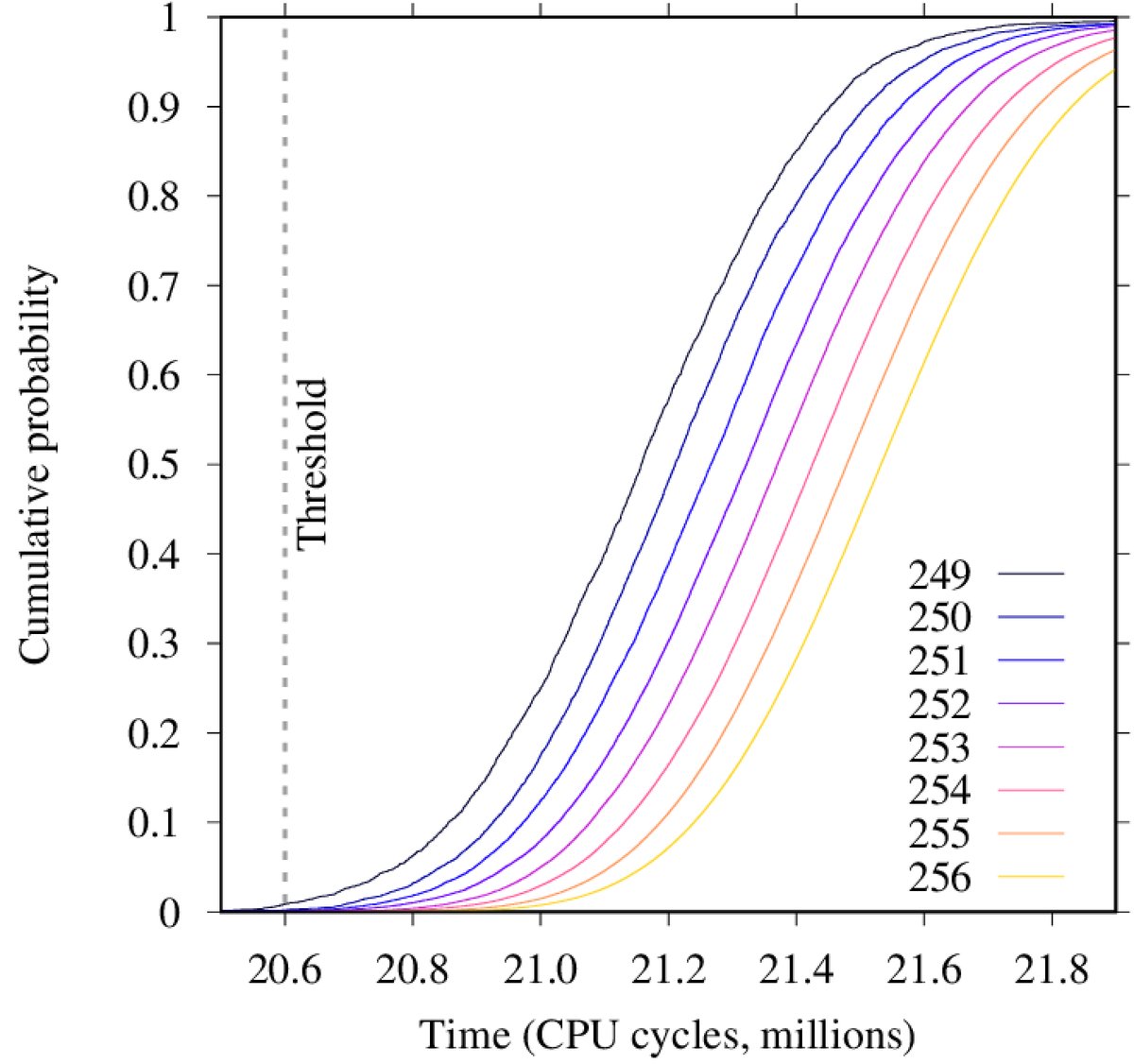
813 Likes, 2 Comments UWMilwaukee (@uwmilwaukee) on Instagram “Happy #PantherPrideFriday 🐾💛 us in your photos to be featured on our page or in our Photos of”. We present the geomagnetic field model COVOBSx1, covering 1840 to , from which have been derived candidate models for the IGRF12 Towards the most recent epochs, it is primarily constrained by first differences of observatory annual means and measurements from the Oersted, Champ, and Swarm satellite missions Stochastic information derived from the temporal spectra of geomagnetic series. From A to Z Projective coordinates leakage in the wild 📺 Abstract Alejandro Cabrera Aldaya Cesar Pereida García Billy Bob Brumley At EUROCRYPT 04, Naccache et al showed that the projective coordinates representation of the resulting point of an elliptic curve scalar multiplication potentially allows to recover some bits of the scalar.
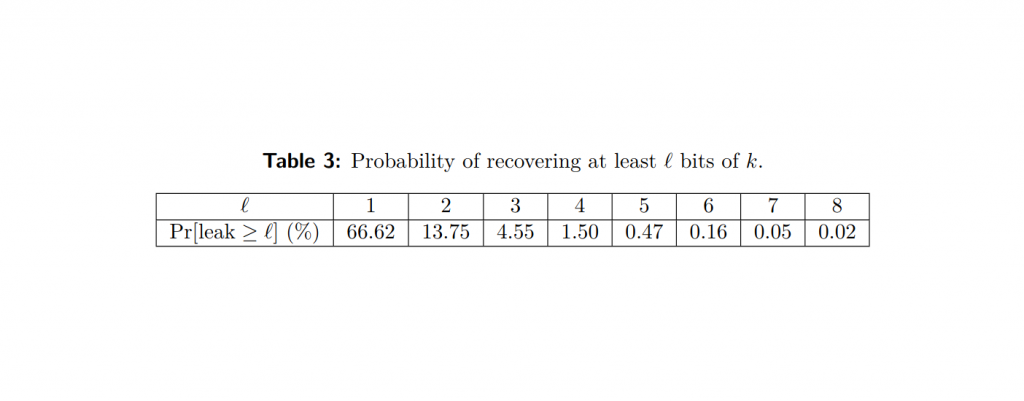
In this case the exact WKB analysis leads to consideration of a new sort of Darboux coordinate system on a moduli space of flat \({\mathrm {SL}}(3)\)connections We give the simplest example of such a coordinate system, and verify numerically that in these coordinates the monodromy of the \(T_3\) equation has the expected asymptotic properties. The con from holes Z9K and Z1062 bored into room 305/2 235 236 tribution made to the total αactivity by U and U and was taken in the southern part of room 012/8 –3 is lower than that made by U by a factor of 15 and 3, (sampling point 35) is within 021–10 mg dm respectively. Nonnegligible leakage and the choice of distance measure Nonnegligible leakage Noisy Sum ε = Ω(1/n) for a constant factor approximation to f(x) Leakage is inherent for statistical utility If ε = ο(1/n) for close databases, then ε=ο(1) for two databases ===> no utility Averagecase distance measures.
Billy Bob Brumley Tampere University;. Abstract Denoting by P=kG the ellipticcurve doubleandadd multiplication of a public base point G by a secret k, we show that allowing an adversary access to the projective representation of P, obtained using a particular double and add method, may result in information being revealed about k Such access might be granted to an adversary by a poor software implementation that does not. In appropriate projective coordinates the Hesse pencil is given by the equation (1) λ (x 3 y 3 z 3) μxyz = 0 The pencil was classically known as the syzygetic pencil 2 of cubic curves (see 9, p 230 or 16, p 274), the name attributed to L Cremona.
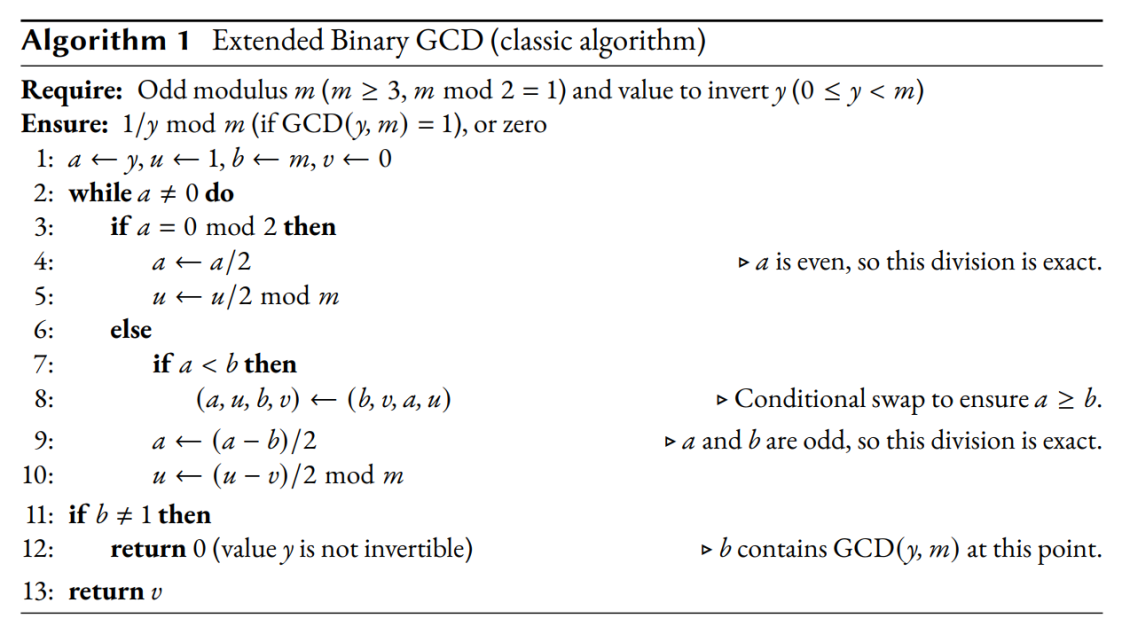
This family of paraboloids has the formula Ω2 r 2 z = zo = r tan 45°, or z o 3333r 2 − r = 0 for a pressure contour 2g The minimum occurs when dz/dr = 0, or r ≈ 015 m The minimum pressure occurs halfway between points B and C Ans (b) Chapter 2 • Pressure Distribution in a Fluid 141. The leakage sources available to the attackers depend on the computing platform libgcrypt a projective coordinates attack, singletrace ECDSA nonce recovery, and recoveryofacountermeasuremask The paper is organized as followsSection 2presents background on elliptic curve. Tl;dr In the context of elliptic curve cryptography To get back from Jacobian coordinates to affine coordinates, you need to compute a multiplicative inverse of a field element, and the binary extended Euclidean algorithm to compute it may leak on side channels A surprising amount of libraries are listed as possibly affected.
Since the only preferred direction in the system is the zdirection, the coordinate system can be rotated such that k y = 0 (without loss of generality), then In what follows, we drop the subscript "x" and use k instead of k x The linearized MHD equations take the form of three equations for the variables v x, v y, and v z, respectively. Emergency evacuations are more common than many people realize, including evacuations in the workplace According to the US Department of Homeland Security (DHS) Federal Emergency Management Agency (FEMA), the most frequent causes of evacuations in the US each year are fires and floods In. Luo et al 04), loop curvature.
Cerebral palsy (CP) is a brain disorder that affects muscle tone and motor skills (the ability to coordinate body movements) A to Z Coxa Valga A to Z Coxa Valga A to Z Failure to Thrive Failure to thrive refers to a child's inability to gain weight and grow as expected for kids of the same age and gender. In exactly one codeword within the specified coordinates xi;. In certain embodiments, to eliminate DC leakage into surrounding AC values, scaling stage within a photo overlap transform operator is modified such that the offdiagonal elements of the associated scaling matrix have the values of 0 In certain embodiments, the ondiagonal scaling matrix are given the values (05, 2) In some embodiments, the scaling is performed using a combination of.
Add open access links from to the list of external document links (if available) load links from unpaywallorg Privacy notice By enabling the option above, your. From A to Z Projective coordinates leakage in the wild Alejandro Cabrera Aldaya and Cesar Pereida García and Billy Bob Brumley Abstract At EUROCRYPT 04, Naccache et al showed that the projective coordinates representation of the resulting point of an elliptic curve scalar multiplication potentially allows to recover some bits of the scalar. In , a Z / p Zcovering of an affine variety Spec A is investigated, and it is shown that if A is a noetherian factorial domain satisfying the condition that every projective Amodule of rank p, p − 1, p − 2 is free then every Z / p Zcovering of Spec A is given as Spec B, where B = A z / (z p − z − a) with a ∈ A.
37 Full PDFs related to this paper READ PAPER Electrical Engineering Handbook. Projective Coordinates Leak October 03 injecting a fault during the projectivetoaffine conversion process so the erroneous results reveals information about Z (third coordinate of a point. Tampere University Defeating StateoftheArt WhiteBox Countermeasures with Advanced GrayBox Attacks.
Title From A to Z Projective coordinates leakage in the wild Authors Alejandro Cabrera Aldaya, Cesar Pereida García, Billy Bob Brumley Venue Cryptographic Hardware and Embedded Systems, CHES , Beijing, China, September 1417,. A generative model G R m ⊇ Z → X ⊆ R n possesses a disentangled representation when it satisfies two important properties (Higgins et al, 16)The first property is orthogonality of the changes in X resulting from perturbations to individual components of a latent variable in ZSuppose that we are given an output x ∈ X, let z \coloneqq G − 1 (x) be the corresponding latent. This document describes the OPAQUE protocol, a secure asymmetric passwordauthenticated key exchange (aPAKE) that supports mutual authentication in a clientserver setting without reliance on PKI and with security against precomputation attacks upon server compromise In addition, the protocol provides forward secrecy and the ability to hide the password from the server, even during password.
Izi 2Z pz can be computed with O(nlogn) operations by FFT interpolation We will use the following Lemma while proving correctness of coefficients of a polynomial Lemma 2 (Schwartz–Zippel) Let pz;qz be two ddegree polynomials from Z pz Then for w $ Z p, the probability that p(w)=z(w) is at most d=p, and the equality can be tested.
Applied Sciences Free Full Text Side Channel Vulnerabilities Of Unified Point Addition On Binary Huff Curve And Its Countermeasure Html
2
Eprint Iacr Org 17 669 Pdf
2
Akiratk0355 Github Io File Slides Wac3 Short Pdf
Cr Yp To Newelliptic Nistecc Pdf
Repository Ubn Ru Nl Bitstream Handle 66 3036 3036 Pdf Sequence 1

Machine Learning For Face Emotion And Pain Recognition
Ninjalab Io Wp Content Uploads 21 01 A Side Journey To Titan Pdf
Ieeexplore Ieee Org Iel7 Pdf

User Authentication On Mobile Devices Approaches Threats And Trends Sciencedirect
2
Ls5fqfqjaz0 Gm

Side Channel Analysis And Countermeasure Design On Arm Based Quantum Resistant Sike

Machine Learning For Face Emotion And Pain Recognition

Cesar Pereida Garcia S Research Works Tampere University Tampere Uta And Other Places

Abstract 19 Basic Amp Clinical Pharmacology Amp Toxicology Wiley Online Library
Repository Ubn Ru Nl Bitstream Handle 66 3036 3036 Pdf Sequence 1

Ecdsa Side Channel Attack Projective Signatures Ledger Donjon Ctf Writeup Cryptohack Blog
Another Paper Accepted At Ches Nisec Tampere Universities
Online Template Attacks Springerlink

Microarchitecture Online Template Attacks Deepai
Akiratk0355 Github Io File Slides Wac3 Short Pdf

Seminar Archive Colorado College
Online Template Attacks Springerlink
Cryptojedi Org Papers Ota Pdf
Cryptojedi Org Papers Ota Pdf
Previous Seminars The Faculty Of Mathematics And Computer Science

Side Channel Analysis And Countermeasure Design On Arm Based Quantum Resistant Sike
Repository Ubn Ru Nl Bitstream Handle 66 3036 3036 Pdf Sequence 1

Pdf From A To Z Projective Coordinates Leakage In The Wild Semantic Scholar

Seminar Archive Colorado College
2

Pdf Microarchitecture Online Template Attacks

Shared Cortex Cerebellum Dynamics In The Execution And Learning Of A Motor Task Sciencedirect
2
Msp Org Obs 4 1 Obs V4 N1 P Pdf
Ieeexplore Ieee Org Iel7 Pdf

State Of The Environment Of The Black Sea 09 14 5
2
Repository Ubn Ru Nl Bitstream Handle 66 3036 3036 Pdf Sequence 1
11th European Headache Federation Congress Jointly With 31st Congress Of The Italian Society For The Study Of Headaches The Journal Of Headache And Pain Full Text

Pdf From A To Z Projective Coordinates Leakage In The Wild Semantic Scholar
Www Siam Org Meetings Is16 Is16 Abstracts Pdf
Manuscriptlink Society File S3 Ap Northeast 1 Amazonaws Com Kiisc Wisa Ec 98 A8 Eb 9d Ec 9d B8 Ed 94 84 Eb A1 9c Ec 8b 9c Eb 94 Pdf
Eprint Iacr Org 17 14 Pdf
Www Tandfonline Com Doi Pdf 10 1080
2
From A To Z Projective Coordinates Leakage In The Wild 哔哩哔哩 つロ干杯 Bilibili
2
Cryptojedi Org Papers Ota Pdf

Pdf Microarchitecture Online Template Attacks
From A To Z Projective Coordinates Leakage In The Wild 哔哩哔哩 つロ干杯 Bilibili

State Of The Environment Of The Black Sea 09 14 5

Side Channel Analysis And Countermeasure Design On Arm Based Quantum Resistant Sike
2
Ftp Ftp Aoc Nrao Edu Pub Software Aips Text Publ Cookbook Pdf

How To Color Complex Functions Domain Coloring Youtube

Same Value Analysis On Edwards Curves Springerlink
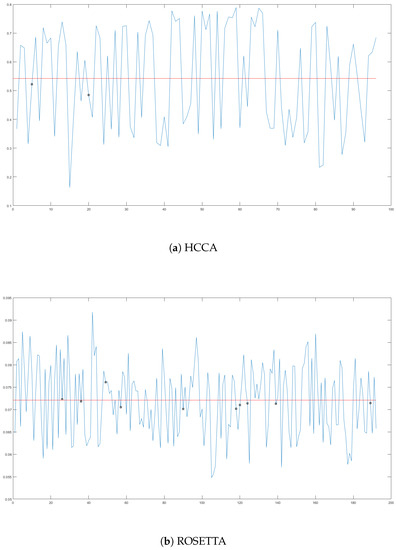
Applied Sciences Free Full Text Side Channel Vulnerabilities Of Unified Point Addition On Binary Huff Curve And Its Countermeasure Html
2
Ninjalab Io Wp Content Uploads 21 01 A Side Journey To Titan Pdf
Cryptojedi Org Papers Ota Pdf
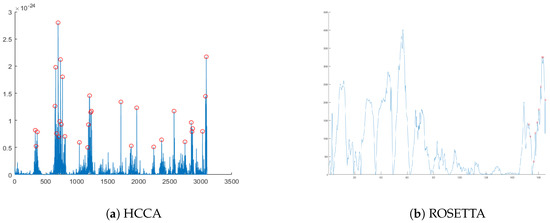
Applied Sciences Free Full Text Side Channel Vulnerabilities Of Unified Point Addition On Binary Huff Curve And Its Countermeasure Html

Abstract 19 Basic Amp Clinical Pharmacology Amp Toxicology Wiley Online Library
2

Topics Archive Openisme

Dip18 2 Hooke Lookbook By School Issuu

Microarchitecture Online Template Attacks Deepai
Ninjalab Io Wp Content Uploads 21 01 A Side Journey To Titan Pdf
2
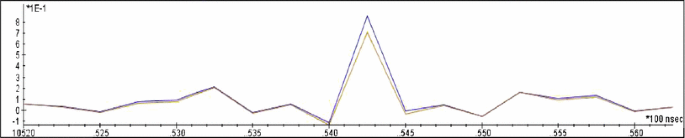
Online Template Attacks Springerlink
Hal Inria Fr Hal Document

Microarchitecture Online Template Attacks Deepai
Arxiv Org Pdf 1707 046
2
Ieeexplore Ieee Org Iel7 Pdf
Repository Ubn Ru Nl Bitstream Handle 66 3036 3036 Pdf Sequence 1

Microarchitecture Online Template Attacks Deepai

Theory Refinement Implications And Conclusions Emerald Insight
Www Osapublishing Org Optica Viewmedia Cfm Uri Optica 7 10 1232 Seq 0
Www Ams Org Journals Notices 0511 0511fullissue Pdf
Osa Cavity Quantum Electrodynamics With Color Centers In Diamond

Alejandro Cabrera Acaldaya Twitter
Hal Inria Fr Hal Document

From A To Z Projective Coordinates Leakage In The Wild Youtube

Alejandro Cabrera Acaldaya Twitter
Akiratk0355 Github Io File Slides Wac3 Short Pdf
2

Alejandro Cabrera Acaldaya Twitter

M8ta Fun
2

Pdf From A To Z Projective Coordinates Leakage In The Wild Semantic Scholar
2



