Cyber Protection

Tac Cyber Protection

World Cyber Protection Week Survey Reveals Most It Pros Back Up Their Data But Still Can T Sleep At Night Acronis Blog

What Is Cyber Security Definition Best Practices

Cyber Security What Think Tanks Are Thinking European Parliamentary Research Service Blog

The Five Ways To Ensure Cyber Security This Christmas

What Is Cyber Security Definition Best Practices More Digital Guardian
Cyber threats are everywhere, and they affect everyone More than 60% of Americans have personally experienced a major data breach (Pew Research Center) The cost of the average data breach to a US company was nearly $8 million (Symantec 19 Internet Security Threat Report).

Cyber protection. Cyber protection ensures that access, while balancing it against the need to keep digital environments and assets safe, private, authentic, and secure Locking a hard drive in a vault makes the contents safe but inaccessible – so it’s not useful. Cybersecurity Biden poised to pick Obamaera security veterans for 3 top cyber roles The leading candidates for the cyber positions have been described as well prepared to confront an ongoing. Cyber Security Strategies Besides understanding cyber law, organizations must build cybersecurity strategies Cybersecurity strategies must cover the following areas Ecosystem A strong ecosystem helps prevent cybercrime Your ecosystem includes three areas—automation, interoperability, and authentication.
Turn challenges into opportunities Stay ahead of modern threats Spend more time focused on your overall security posture, rather than on managing the Gain proactive cyber protection Avoid downtime, prevent loss of employee productivity, and spend less time on costly Eliminate unnecessary. Make it safer for your business to innovate As one of the world’s largest Managed Security Services Providers (MSSP), AT&T Cybersecurity delivers the ability to help safeguard digital assets, act with confidence to detect cyber threats to mitigate business impact, and drive efficiency into cybersecurity operations. Cyber security is the state or process of protecting and recovering networks, devices and programs from any type of cyberattack Cyberattacks are an evolving danger to organizations, employees and consumers They may be designed to access or destroy sensitive data or extort money.
Extorting money from users;. The IP behind Covid19 vaccines and their supporting supply chains need stateoftheart protection comprised of cybersecurity technologies and systems, as the vaccines' IP is an asset that cyber. Cyber security is the practice of defending computers, networks, and data from malicious attacks Learn the skills, certifications and degrees you need to land a job in this challenging field.
The IP behind Covid19 vaccines and their supporting supply chains need stateoftheart protection comprised of cybersecurity technologies and systems, as the vaccines' IP is an asset that cyber. Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access In a computing context. Cyber Security is a set of techniques that are used to protect the internetconnected systems It can protect computers, networks, software, and data Cyberattacks are performed to make unauthorized access, change or destroy data, or to extort the money.
Cyber Security is National Security Home » Cyber Security is National Security After the President released the National Cyber Strategy in 17, Energy Secretary Brouillette clearly stated, “Advancing cybersecurity is a core priority for the Department of Energy”. Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access In a computing context. Home > Training > Youth Protection > Cyber Chip Cyber Chip Today’s youth are spending more time than ever using digital media for education, research, socializing, and fun To help families and volunteers keep youth safe while online, the Boy Scouts of America introduces the Cyber Chip In developing this exciting new tool, the BSA teamed.
One way to start this process is to take advantage of the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICSCERT) ICSCERT provides a wide range of information, tools, and services that can help companies assess their security, identify recommended practices, and improve their cyber security http//icscertuscertgov/. Security controls between each level are typified by a “demilitarized zone” (DMZ) and a firewall Conventional approaches restrict downward access to Level 3 from Levels 4, 5 (and the internet) Heading upward, only Layer 2 or 3 can communicate with Layers 4 and 5, and the lowest two Levels (machinery and process) must keep their data and. Cyberattacks are a serious economic and security threat To combat both immediate and future dangers, businesses and governments are investing in cyber security Understanding trends in cybersecurity and how machinelearning techniques defenses can respond to threats is a critical component of protecting networks, infrastructure and users.
Although cyber insurance is a growing market, standalone personal cyber insurance policies have yet to gain traction The most prominent insurer to offer comprehensive cyber protection is State Farm, with its Cyber Event, Identity Restoration and Fraud Loss coverage This coverage can be purchased as an addon to State Farm home insurance. Make it safer for your business to innovate As one of the world’s largest Managed Security Services Providers (MSSP), AT&T Cybersecurity delivers the ability to help safeguard digital assets, act with confidence to detect cyber threats to mitigate business impact, and drive efficiency into cybersecurity operations. Cyber Protection, which protects your business against damage caused by a virus or computer attack, as well as helping with the cost of restoring and recreating data We also offer tips to help you manage your computer and technology risks resulting from data loss, data breaches, denial of service attacks, malware, viruses and more.
Cybersecurity Biden poised to pick Obamaera security veterans for 3 top cyber roles The leading candidates for the cyber positions have been described as well prepared to confront an ongoing. Predict Adapt Synchronize Advanced Endpoint Protection and Network Security Fully Synchronized in Real Time Sophos is Cybersecurity Evolved. Cyber personal protection Covers breaches of privacy, cyber bullying and cyber disruption, the latter referring to events that prevent you from accessing your home or interrupting a small business you run from your home.
Cyber Security Readiness Small to midsized businesses often lack the resources to keep up with new cyber threats Strengthen your operational security posture with an assessment and an actionable plan to improve upon your strengths and address your vulnerabilities. Securing cyberspace is a 24/7 responsibility, and every individual is the first line of defense For resources to help keep personal and professional online experiences safe, visit our fact sheets. Biden intends to nominate Rob Silvers, who was the Obama administration's assistant secretary for cyber policy at the Department of Homeland Security, to fill Krebs' role, Reuters reported.
To help families and volunteers keep youth safe while online, the Boy Scouts of America introduces the Cyber Chip In developing this exciting new tool, the BSA teamed up with content expert NetSmartz®, part of the National Center for Missing and Exploited Children® and training expert for many law enforcement agencies. Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information;. One Subscription & Unlimited Device Protection From Internet Threats at Home and OnTheGo NETGEAR Armor is multilayer cybersecurity with subscriptions starting at $9999 $6999 and is available exclusively on Orbi Mesh WiFi Systems and Nighthawk Routers.
Cyber insurance is a subcategory of general insurance that covers businesses and individuals against internetbased liability and risks There are generally two levels of cyber liability coverage. The National Cybersecurity Protection System (NCPS) is an integrated systemofsystems that delivers a range of capabilities, such as intrusion detection, analytics, information sharing, and intrusion prevention These capabilities provide a technological foundation that enables the Cybersecurity and Infrastructure Security Agency (CISA) to secure and defend the Federal Civilian Executive Branch (FCEB) agencies' information technology infrastructure against advanced cyber threats. Make it safer for your business to innovate As one of the world’s largest Managed Security Services Providers (MSSP), AT&T Cybersecurity delivers the ability to help safeguard digital assets, act with confidence to detect cyber threats to mitigate business impact, and drive efficiency into cybersecurity operations.
Cyber Protection, which protects your business against damage caused by a virus or computer attack, as well as helping with the cost of restoring and recreating data We also offer tips to help you manage your computer and technology risks resulting from data loss, data breaches, denial of service attacks, malware, viruses and more. Predict Adapt Synchronize Advanced Endpoint Protection and Network Security Fully Synchronized in Real Time Sophos is Cybersecurity Evolved. Malicious cyber activity threatens the public’s safety and our national and economic security The FBI’s cyber strategy is to impose risk and consequences on cyber adversaries Our goal is to.
CYBERSECURITY CISA leads the Nation’s strategic and unified work to strengthen the security, resilience, and workforce of the cyber ecosystem to protect critical services and American way of life. Supplier Cyber Protection Service This service allows the Ministry of Defence (MOD) and industry partners to manage cyber risk across the defence supply chain Published 2 October 17. The US Army Cyber Protection Brigade (CPB), the first of its kind in the Army, was activated at its home station at Fort Gordon, Georgia, on Sept 5, 14 The CPB's mission is to defend key.
Protect an unlimited number of smart devices* from cyber threats with a single subscription NETGEAR Armor™ provides multilayered cybersecurity on your smartphones, computers, smart TVs, security cameras, and anything else connected in your home. Definition Cyber security or information technology security are the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation Description Major areas covered in cyber security are 1) Application Security 2) Information Security 3) Disaster recovery 4) Network Security. Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access Cyber security may also be referred to as information technology security The Importance of Cyber Security.
Although cyber insurance is a growing market, standalone personal cyber insurance policies have yet to gain traction The most prominent insurer to offer comprehensive cyber protection is State Farm, with its Cyber Event, Identity Restoration and Fraud Loss coverage This coverage can be purchased as an addon to State Farm home insurance. Definition Cyber security or information technology security are the techniques of protecting computers, networks, programs and data from unauthorized access or attacks that are aimed for exploitation Description Major areas covered in cyber security are 1) Application Security 2) Information Security 3) Disaster recovery 4) Network Security Application security encompasses measures or. Cyber attacks are a growing concern for small businesses Learn about the threats and how to protect yourself.
This is why DOE is committed to working with the private sector to increase cyber security and resiliency in the prevention of cyberattacks In 18, Secretary Brouillette signed and endorsed the Cybersecurity Strategy of 10, a strategy that outlines the vision to secure the Department of Energy. Cybersecurity standards are techniques generally set forth in published materials that attempt to protect the cyber environment of a user or organization This environment includes users themselves, networks, devices, all software, processes, information in storage or transit, applications, services, and systems that can be connected directly or indirectly to networks The principal objective is to reduce the risks, including prevention or mitigation of cyberattacks These published materials c. Make it safer for your business to innovate As one of the world’s largest Managed Security Services Providers (MSSP), AT&T Cybersecurity delivers the ability to help safeguard digital assets, act with confidence to detect cyber threats to mitigate business impact, and drive efficiency into cybersecurity operations.
Cybersecurity Biden poised to pick Obamaera security veterans for 3 top cyber roles The leading candidates for the cyber positions have been described as well prepared to confront an ongoing. As the nation's risk advisor, the Cybersecurity and Infrastructure Security Agency (CISA) brings our partners in industry and the full power of the federal government together to improve American cyber and infrastructure security Since the beginning of the Coronavirus threat, also known as COVID19, CISA has been monitoring the evolving virus. Or interrupting normal business processes.
How to protect yourself against cybercrime 1 Use a fullservice internet security suite For instance, Norton Security provides realtime protection against 2 Use strong passwords Don’t repeat your passwords on different sites, and change your passwords regularly Make them 3 Keep your.

Pa Business One Stop Shop Cyber Security And Privacy Protection In The Time Of Pandemic

Critical Information Systems And Cybersecurity Thales Group

Small Business Cyber Security An Essential Guide

Cyber Security And Data Protection

Reason For Using Artificial Intelligence In Cyber Security Cyberdb

A Moment Of Reckoning The Need For A Strong And Global Cybersecurity Response Microsoft On The Issues

Strong Leadership Is A Company S Best Cyber Protection Lloyd S List

Cyber Security Data Protection And Privacy Abla

How To Protect Your Small Business From Cyber Attacks Bytestart

The Top 25 Cybersecurity Companies Of 19 The Software Report

Threat Protection Choosing A Cyber Security Partner

Cybersecurity Universita Di Padova

W Series And Acronis Announce Cyber Protection And Security Partnership Motorsport Technology

Convergint Is Offering A Free Trial Of Cyber Protection Plus For 45 Days Convergint

Imo 21 Puts A Spotlight On Cyber Security Marine Offshore

Cyber Security Protection 7 Steps Ship Operators Can Take Now Shipinsight

Cybersecurity Emerson Us
.jpg)
Nas Announces New Cyber Protection For High Net Worth Individuals Insurance Business

Acronis Acquires Cyberlynx Enhances Cyber Protection Portfolio With Additional Security Services Financial It

Best Cybersecurity Website Protect Your Site With Cwatch Security

Brexit The Implications For Cyber Security And Data Protection Institute Of Directors Iod

Cyber Security Wdigital

Importance Of Cyber Security Protection For Australian Businesses

Covid 19 Is Accelerating The Digital Transformation Of Cyber Security

Cybersecurity Information Protection At Ccm Cyber Security Information Protection

Free Vector Cyber Security Flyer Square
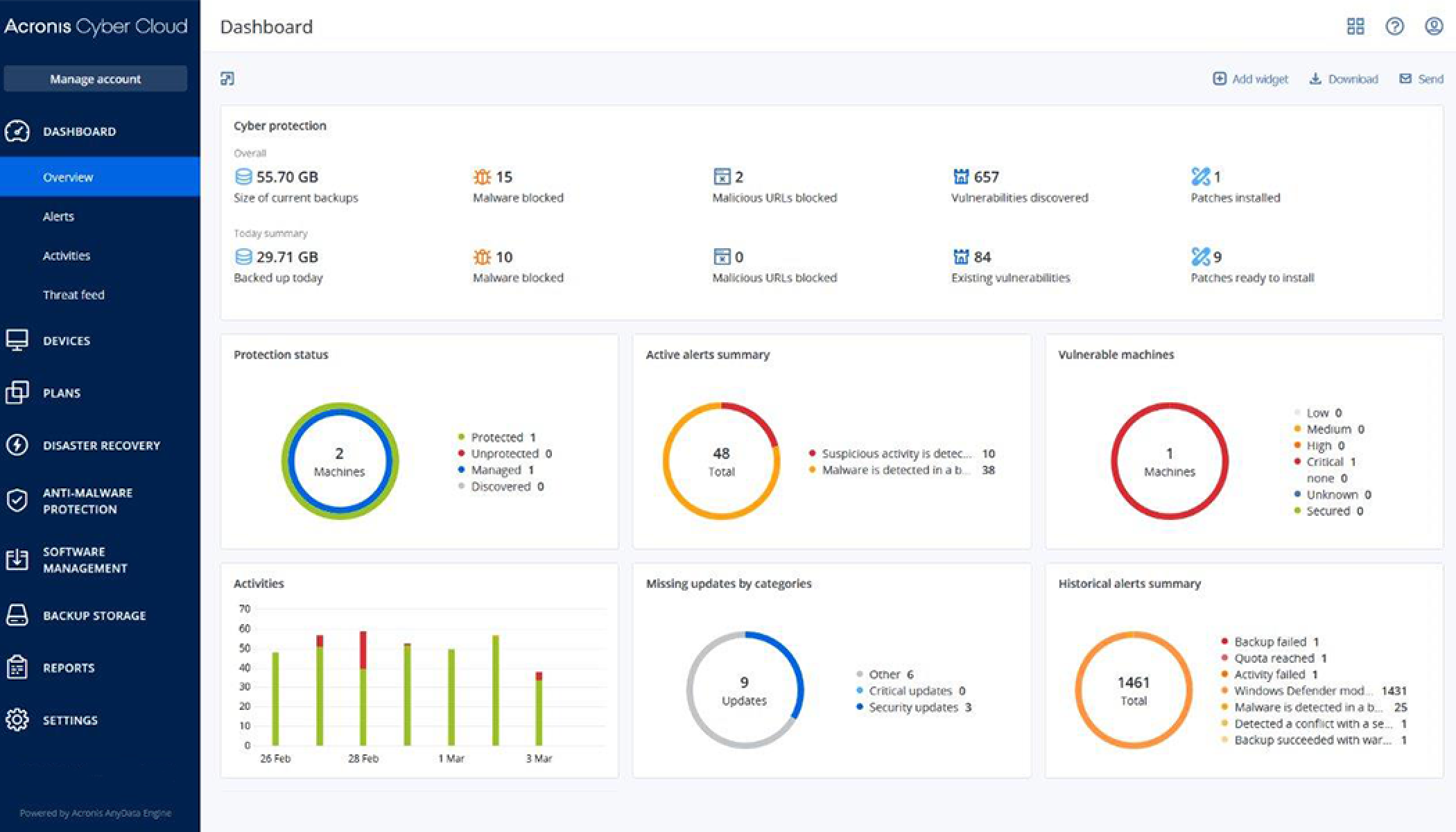
Singapore Unicorn Acronis Released The World S First Complete Cyber Protection Solution Tailored To Fight Pandemic Cyberthreats And Improve Remote Work

5 Essential Cyber Security Themes Fermanagh Enterprise Limited

Top 11 Most Powerful Cybersecurity Software Tools In 21

The Human Side Of Cyber Security From Threat To Defender Ibm Big Data Analytics Hub

Comparing Top 11 Cyber Protection Solutions For Businesses

Cybersecurity Talent The Big Gap In Cyber Protection

Business Man On Laptop Cyber Security Banner Download Free Vectors Clipart Graphics Vector Art

Comarch Cyber Security Software Solution Find Out More

Itwire Acronis Cyber Protect 15 Total Cyber Protection Needed As 31 Of Companies Face Cyber Attacks Daily
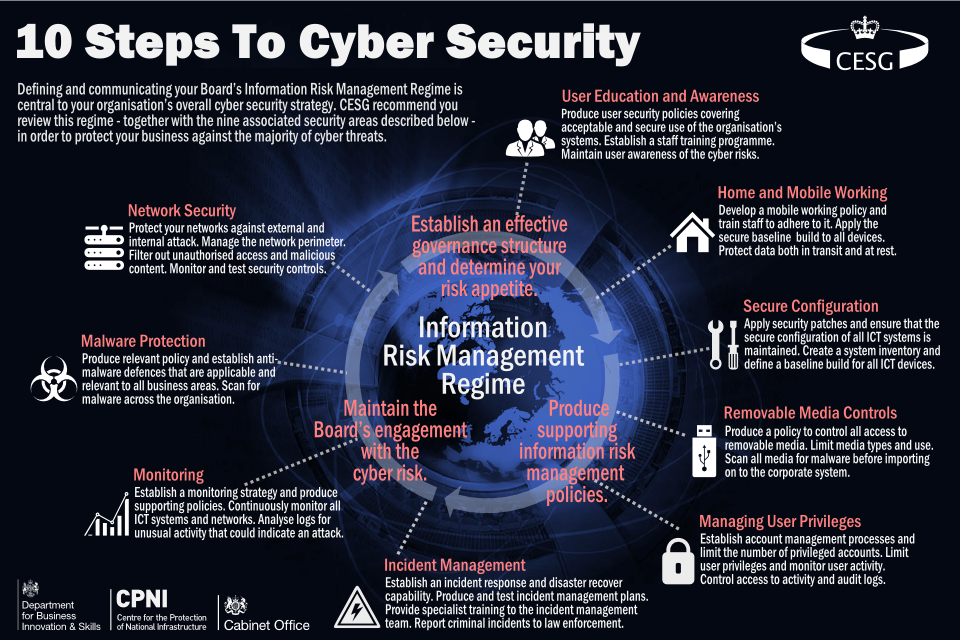
Withdrawn 10 Steps Summary Gov Uk

Modern Cyber Protection 5 Vectors You Need To Know Znetlive Blog A Guide To Domains Web Hosting Cloud Computing

5 Cyber Security Trends In Businesses Need To Know Mybusiness

Awareness Is Key To Aviation Cyber Protection Embry Riddle Aeronautical University Newsroom

What S The Difference Between Cyber Security And Information Security By Michael Warne Medium

Royal Navy Brings Cyber Protection Into The Spotlight Safety4sea

Assured Cyber Protection Acp Technology Twitter

Cyber Protection Full Range Of Cyber Protection Solutions Acronis

Guest Blog Data S Value To Businesses Demands The New Approach Of Cyber Protection Acronis Blog

What Are The Types Of Cyber Security Vulnerabilities Logsign

Taking Advantage Of Ai In Cyber Security Strategies Cyber Security Hub

These Cyber Protection Tips Can Help Keep Your Business Safe Personal Insurance Business Insurance Cd G Insurance In Oakland

Cyber Security Threats In The Food Beverage Industry Sobelco

How To Land The Best Jobs In Cyber Security Includes Salary Data

Latest Maritime Cyber Security And Threats Safety4sea

Premium Vector Cyber Security Instagram Posts

71 231 Cyber Security Illustrations Royalty Free Vector Graphics Clip Art Istock
30 Cyber Security Awareness Tips Your Business Needs
%20FINAL.jpg?width=993&height=2423&name=6%20point%20cyber%20security%20checklist%20vertical%20version%20(4D)%20FINAL.jpg)
Infographic Cyber Security Checklist For 19

Cyber Security For Fire Protection Systems Ul

Cyber Protection Services Linkedin

Cyber Security Solutions Cyber Security Protection Services

Cyber Security Strategy And Response Fieldfisher

Telefonica Backs Nozomi In Latest Cybersecurity Move Mobile World Live

Acronis Makes Remote Work Environments More Secure Launches Acronis Cyber Protect

Maintaining Your Mission The Need For Complete Cyber Protectionwebinar

Axa Xl Accenture Partner To Provide Cyber Security Services To Axa Xl Clients

Cyber Security Job Types Careersincyber Com

Future Cyber Security Protection Reflection From The Ups And Downs Of Covid 19 1 Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks

Grid Security Energy Automation And Smart Grid Siemens Global

Cybersecurity Solutions Atos

Threat Protection And Cyber Security Recruitment Jonathan Lee

G27dbizeaszrcm
Q Tbn And9gcsa6tz Vdol3rw13hqpzmyfhyx G3f2tl Qituymya Usqp Cau

How Ai Ml And Automation Can Improve Cybersecurity Protection Techrepublic

Government And Water Industry Warned Of Cyber Security Blind Spots International Water Power

Cyber Security Omicron

Pensions And Cyber Security Is The Industry Addressing The Risks Fieldfisher

Taking Responsibility For Cyber Security In A Truly Virtual World

Top 15 Tips To Improve Cyber Security Telappliant

Full Recording An Enlightened Approach To Cyber Protection Friedman Llp

What Is Cyber Security Definition Types And User Protection Kaspersky

Cyber Security

Grow Your Msp Or Var Business With Cyber Protection Services Channel Futures

Global Open Standards For Cyber Security Beyond Standards

Understanding Modern Cyber Protection What You Need To Know Acronis Blog

How To Practice Cybersecurity And Why It S Different From It Security Cso Online
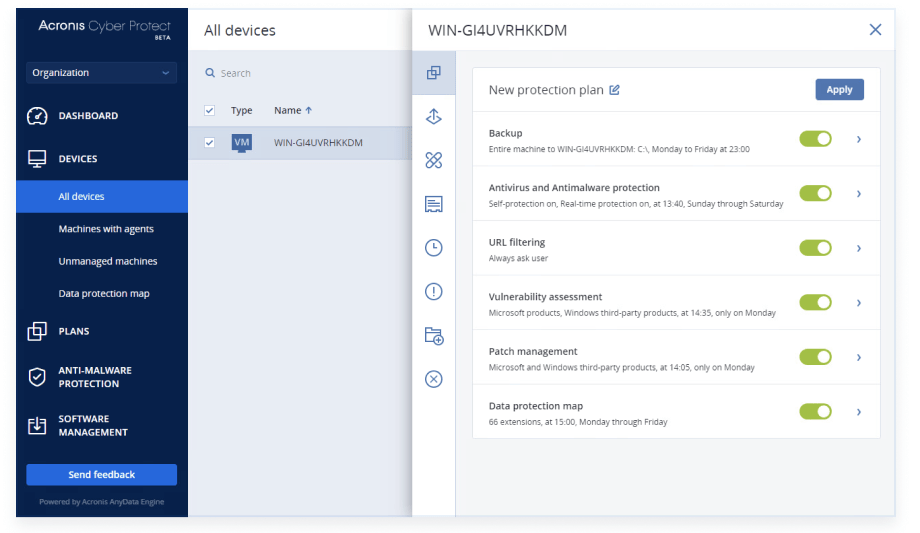
Acronis Launches Cyber Protect 15 Cybersecurity Solution Security News Sourcesecurity Com
Q Tbn And9gctcqug93ztsenn3uzr2dvi169pik Lrcrm Hwxp Fuityq4x0q Usqp Cau
3

Steamship Mutual Cyber Security And Data Protection

Why Businesses Must Make Cyber Security Skills A Priority In 17 Information Age

Acronis Cyber Protect Cloud World S First Complete Cyber Protection Solution In The Remote Work Era Znetlive Blog A Guide To Domains Web Hosting Cloud Computing

Cyber Security Courses Study Online With Top Universities Futurelearn

Us Citizens Want Government To Strengthen Cyber Protection Smart Cities World

How To Protect Your Practice From Cyber Attacks With Cyber Security

Why Is Cyber Security Important It Company Birmingham

Master Of Science In Security Studies Cybersecurity Concentration Online Criminal Justice Security Studies Major Umass Lowell

The Three Pillar Approach To Cyber Security Data And Information Protection Dnv Gl

Acronis Delivers Cyber Protection Where Data Protection And Cybersecurity Merge Youtube

Cybersecurity In Europe Stronger Rules And Better Protection Consilium

Assured Cyber Protection Acp Linkedin



